Ransomware attacks have been on the rise in recent years, with industry estimates reporting a fourfold increase in payments made to cybercriminals in 2020 and 2021 compared to 2019.
These attacks have had a significant impact on society, causing major disruption and damage to governments, public institutions, businesses, and citizens. In some cases, ransomware attacks have even impacted healthcare systems and threatened national security by stopping critical infrastructure and services or compromising sensitive data.
As the frequency and severity of ransomware attacks continue to increase, it is crucial to understand their effects on society and how to prevent and mitigate them.
In response to the growing threat of ransomware attacks, the Financial Action Task Force (FATF) has issued a “Countering the Financing of Ransomware” report that provides guidance for countries to prevent and detect the laundering of proceeds from these attacks. Additionally, it has issued potential risk indicators for financial institutions and other businesses to help identify and report suspicious activity related to ransomware payments.
What is Ransomware?
Ransomware is a type of extortion where attackers use a type of malicious software (malware) that criminals use to deny access to data, systems, or networks while demanding a ransom payment in exchange. Attackers commonly employ various methods to deny access to data such as data encryption, data exfiltration, etc.
What sets ransomware apart from other types of malwares is the threat to publish the victim’s data if the ransom demand is not met. As such, ransomware attacks can cause significant disruptions, losses, and even reputational damage for businesses, institutions, and individuals alike.
Ransomware Techniques
Ransomware techniques have evolved significantly in recent years, with criminals utilising sophisticated methods to access their victims’ systems.
These techniques often involve:
- Big game hunting: This technique involves targeting large, high-value organisations, often high-profile ones that are more likely to have higher costs of downtime, including critical infrastructure. These organisations are believed to have a higher probability of paying ransoms. Ransomware attackers frequently target energy, banking, communication, and education sectors, but they also target government/public sector entities, healthcare, and industrial goods.
- RAAS: This stands for Ransomware-as-a-Service, which is a business model where ransomware criminals either provide ransomware services on the Dark Web or outsource elements of the attacks, such as distribution of malware, initial compromise of a victim’s network, stolen credentials, and other services in exchange for a fee.
- Double extortion: This technique involves an attacker exfiltrating a victim’s data before encrypting it and then threatening to publish the stolen data if ransom is not paid.
- Triple extortion: This technique involves an attacker asking for ransom not only from the victim company but also from the victim whose data was disclosed. This might include protected health information, personally identifiable information, account credentials, and intellectual property.
- Multiple extortion: This practice involves more than two extortion methods. It may include double-extortion using encryption, but also additional pressure tactics such as distributed denial-of-service (DDoS), contacting victims’ customers, short selling victims’ stocks, and disrupting infrastructure systems.
Ransomware attacks can have severe consequences and pose significant national security threats, including causing damage and disruption to critical infrastructure and essential services.
Countries with Higher Risk of Laundering Ransomware Attacks
Ransomware attacks are a global problem, but certain countries are at higher risk of being targeted by these malicious actors to launder the proceeds of their crimes.
These countries include:
- Countries known for providing funding or support to terrorism activities
- Countries known for having significant levels of organised crime, corruption, drugs, human trafficking, and illegal gambling
- Countries subject to sanctions, embargoes, or similar measures
- Countries with weak governance, law enforcement, and regulatory regimes, especially VASPs
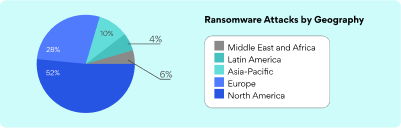
Geographical Distribution of Ransomware Attacks
The distribution of ransomware attacks refers to the geographical spread of these types of attacks. Different regions have different levels of susceptibility to these attacks due to variations in security measures and digital infrastructure. According to the FATF, North America seems to have the higher ransomware attacks where Middle East and Africa the lowest.
Methods of Laundering Proceeds from Ransomware Attacks
Ransomware attackers often demand payments in virtual assets, making it difficult to trace the illicit proceeds. Criminals employ a range of techniques to launder the virtual assets they receive as payments for ransomware attacks. These methods aim to conceal the origin and movement of the illicit funds, making it difficult for law enforcement authorities to track and seize them and include:
- Peer-to-peer (P2P): The victim can send virtual assets to the ransomware operator directly with the use of their private key and internet connection without the use of a regulated institution. As a result, the parties of the transaction do not need to go through KYC procedures.
- Different wallet addresses: Ransomware attackers often demand payments in different wallet addresses they control to receive illicit proceeds from each attack.
- Use of intermediary addresses: Once funds are received, the attackers may use multiple intermediary addresses to move the virtual assets by transferring small amounts to new addresses hosted by regulated VASPs (peel chains).
- Use of mixers and tumblers: These services conceal the connection between the virtual asset sending address and the receiving address.
- Privacy coins: Although most ransomware attackers demand their payments in bitcoins, in some cases they request their payments in privacy coins (anonymity-enhanced cryptocurrencies). These coins obfuscate sending and receiving wallets.
- Chain-hopping: Ransomware attackers often move virtual assets from one blockchain to a different blockchain in rapid succession to evade tracking of movements. In some cases, they use DeFi protocols to chain-hop into stablecoins before converting the funds into fiat currency.
- VASPs in high-risk jurisdictions: Often attackers send the virtual assets to a VASP located in jurisdictions with weak or non-existent AML/CTF controls to make the conversion into fiat currency.
- Money mules: Often criminals open accounts using a stolen or fake identity or use accounts held by third parties who are recruited for this purpose. These accounts are used to move funds further disguising the source of the virtual assets.
Proposed practices by the FATF in Relation to Ransomware Attacks
To effectively combat the increasing threat of ransomware attacks, various practices have been proposed by the FATF for countries to adopt. These measures aim to enhance detection, prevention, and prosecution of ransomware attacks and the laundering of their proceeds by requiring countries to:
- Criminalise ransomware as a predicate offence
- Accelerate the regulation of Virtual Asset Service Providers (VASPs) for AML/CFT purposes and ensure that they comply with the Travel Rule and reporting of suspicious transactions. The limited implementation of the Travel Rule by VASPs presents opportunities for cybercriminals to avoid detection and hinder investigations, as law enforcement relies on this information to identify the parties involved in a transaction
- Enhance detection by providing guidance to regulated entities to detect ransomware and suspicious transactions by sharing trends, guides and red flag indicators but also encourage victims to report ransomware incidents
- Ensure that law enforcement investigates, traces and confiscates criminal proceeds
- Establish mechanisms that support public-private sector cooperation
- Improve international cooperation
Methods for Detecting Ransomware Attacks
Often, competent authorities use the following sources of information to collect information about ransomware attack incidents.
- Regulated institutions such as Banks and VASPs (from suspicious transaction reports)
- Non-regulated sectors (i.e., institutions involved in ransomware and cybercrime)
- Incident response companies (i.e., digital forensic incidence response companies and law firms)
Potential Risk Indicators for Detection of Ransomware
To combat the increasing threat of ransomware attacks and their financing the FATF has developed some risk indicators to aid countries in detection of ransomware attacks. These risk indicators provided by the FATF are based on specific behaviours and transactions that may indicate ransomware activity, and can be used by financial institutions, regulators, and law enforcement to identify and investigate suspicious activity.
Indicators for Financial Institutions and Payment Systems
- Wire transfers out to ransomware remediation specialists in the cybersecurity consulting and incident response industries.
- Wire transfers from insurance firms specialising in ransomware cleanup that arrive out of the blue
- Client-reported ransomware incidents and payments
- Client ransomware attacks open-source data
- Large numbers of withdrawals and deposits at a VASP using the same bank account
- Words like “ransom”, or the names of known ransomware families appear in the description of the payment.
- Funds disbursed to VASPs in countries with a high risk of corruption
- Using VASPs to track ransomware victims who have paid:
- A third-party’s request for an incident response or insurance business to purchase virtual assets.
- The customer informs the VASP that they must pay the ransom to purchase virtual assets.
- A user with no prior record of sending or receiving virtual assets sends money outside of normal protocol.
- A customer raises their account limit and transmits the additional funds to another party.
- The customer appears worried or agitated about the delay in receiving money.
- Payments made to VASPs in high-risk areas; Purchases or transfers of cryptocurrency that increase users’ anonymity
- When a new customer buys virtual assets, they send their whole account balance to a single location.
- Evidence-based strategies for preventing ransomware:
- After an initial, sizable exchange of virtual assets, the buyer engages in almost no more transactions in virtual money.
- Using blockchain technology, we can trace ransomware through victim wallet addresses.
- Instant access to funds following virtual asset conversion
- Transfer of virtual assets to ransomware-associated wallets
- Using a VASP in a dangerous country
- Sending Virtual Assets to a Music Production Service
- Using a secure connection
- The verification data is a screenshot or a filename that includes “WhatsApp image” or something like.
- Syntax of client does not match customer’s age range
- Data on the customer reveals the presence of a proton mail or similarly discreet email address.
- Inconsistent information provided for identification or an effort to create a fake account
- The same contact information is used for multiple accounts, and addresses are used interchangeably.
- An apparently VPN-using customer
- The use of anonymous cryptocurrency transactions
What the Future Holds
We can expect to see continued efforts by the FATF and other international organisations to combat the growing threat of ransomware attacks and the laundering of proceeds from these attacks.
On their side, governments and businesses will need to implement more robust security measures to protect against ransomware attacks and be prepared to respond quickly and effectively if an attack occurs.
Additionally, we may see increased cooperation and information sharing among countries and law enforcement agencies to identify and track down cybercriminals involved in ransomware attacks. Ultimately, preventing and mitigating ransomware attacks will require a comprehensive and collaborative approach from all stakeholders involved.


0 Comments